I Played This Free Linux Skills Game and Learned 6 New Commands

I am a big fan of gamified learning. It led me to try a popular Linux learning game: Overthewire. What started as a rapid curiosity has been transformed into hours of puzzle resolution, terminal magic and the kind of “AHA!” The moments you only get when you can’t find something for real.
Why I love it so much too much
Overthewire is a collection of war games. War games are essentially CTF style challenges where you have to perform a special task to get a special token as proof that you have erased this level. In the context of Overthewire Bandit, which I will mainly talk about, you must look for and find a secret password to go to the next level.
I have explored many games that teach Linux so far. But Overthewire really stands out due to the implementation of his environment and the way he questions your knowledge in real challenges based on scenarios. You fell into real Linux systems to explore. Whether you are new to Linux or an intermediate user, there is something for you in the game.
The levels are designed to increase smoothly in difficulty. One thing that I admire is that a particular level can also require orders and techniques from the previous levels. This helps you keep your learning longer and solidify it.
What I like most about Overthewire is how he treats you as a capable learner. He is not trying to transform you into a robot that memorizes orders and techniques. On the contrary, this helps you become someone who can investigate, solve problems and reason through unknown territory. These are skills that go beyond the terminal and appear everywhere in technology.
He teaches you the most important Linux competence
If there is one thing that Overthewire teaches better than any YouTube tutorial or video, it is to learn to understand things for yourself.
When you play Bandit, the game does not hold your hand. We tell you what is your goal, and you could get a clue or two on the orders could help. But that’s it. There is no step-by-step procedure in the level, no small offense explaining the functioning of the XYZ command, and certainly no pop-up showing you the exact syntax to use. You have to go get it. You have to try, fail, modify your approach and try again. And that’s exactly what makes him so good.
For me, it is essential Linux competence. Agree not to know something, then understand it by looking for, reading the pages and experimenting. This is the kind of competence that separates someone who simply copies Stack overflow commands from someone who understands what he really does.
You learn more than Linux commands
Overthewire does not only concern Linux orders. Even if Bandit is technically on this subject, the truth is that you end up learning much more than a simple syntax.

Related
15 unnecessary Linux orders that everyone needs to know
All true Linux Pro should know these 15 unnecessary orders!
For example, you are exposed to things such as file authorizations, network protocols, Internet technology and text encoding. I had to decode hexagonal channels, take a look inside strange binary files, connect to dark ports and understand how the Linux file system is structured at a deeper level.
Once you have finished Bandit, Overthewire opens even more. The Leviathan is entering the climbing of privileges. There is Narnia, who plunges into the exploitation of memory and the overflows of buffer. Krypton focuses on the basics of cryptography. The labyrinth contains engineering and opposite operating challenges. Each wargame is based on a different aspect of security, programming or other IT concepts.
Orders that I learned
Now, I wouldn’t say that Overthewire was the very first place where I saw these commands, but it was the first time in a while that I had to use them with a goal. Some that I had partially forgotten how to use, others that I had only used with a syntax with a copy and a vague idea of what was going on. Playing at Bandit forced me to slow down and learn what each command really does, and how to use them more intelligent and more intentional. Here are six that stood out.
Related
11 neglected linux commands that you should really use
These orders could considerably improve your workflow!
ssh
SSH means Secure Shell. It is the standard way to connect remotely to the terminal of another machine, especially on the Internet. It’s like teleporting your command line session to another computer, safely and encryption, so that your data and password are not exposed during transit. Here is the most basic syntax of the SSH command:
ssh username@hostname
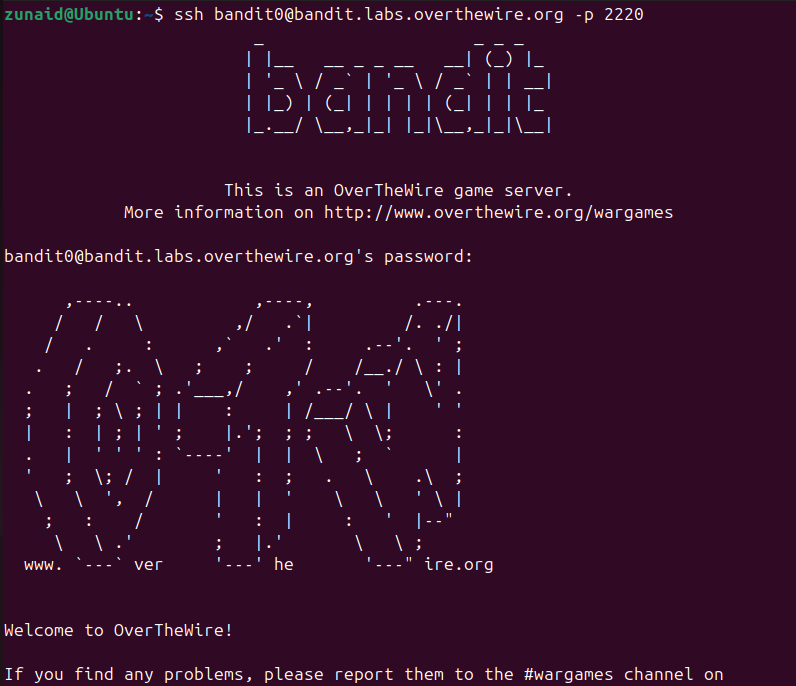
SSH is the first command you would use in Overthewire Bandit. In fact, you should even use it to start, because you have to connect to their server to play the game. You have to use it at all levels, so it becomes your second nature. Here’s how:
ssh bandit0@bandit.labs.overthewire.org -p 2220
Here, you connect to the Bandit.labs.Overthewire.org server as a bandit0 user on port 2220. Once connected, you get a shell on this remote machine and access the system.
find
Find is a command line to search in directories and locate files that match specific criteria such as name, size, authorizations, modification time, etc. It’s a bit like the Linux version of a research function, but much more powerful. Basic syntax:
find [path] [options]
For example, let’s say you want to search for a file called “password.txt”. Here is the order on this subject:
find . -name "password.txt"
This indicates in search of looking in the current repertoire (.) And all its sub-directories for a file called exactly Password.txt. In one of the first levels of bandit, you had to search for a file readable by humans, 1033 bytes and not executable. The Find command was adapted to this scenario.
find dir_name -type f -size 1033c ! -executable
This is looking for files in the particular directory which are exactly 1033 bytes (C represents bytes) and excludes non -executable files.
sort
The sorting command line utility organizes lines of text in a specific order. It can be alphabetical, digital or on the basis of other rules that you define. It is deceptively simple, but when combined with other tools like UNIQ, CUT or AWK, it becomes a power for the processing of text data. The basic syntax is as follows:
sort [options] [filename]
For example:
sort file.txt
This will sort alphabetically the lines in File.txt and print them to your terminal. In one of the levels, you meet a file containing many passwords. To find the right one quickly, you must have sorted the file in alphabetical order and filter the unique values. The sorting command was useful for this:
sort data.txt | uniq -u
Since UNIQ only works on consecutive double lines, we must first sort it. Now it will only come out lines that appear exactly once.
xxd
The XXD command creates a hexagonal emptying of a file or converts hexagonal emptying into its original binary form. It is a bit of a niche utility, but extremely useful when you are dealing with hidden data, encoded files or trying to inspect the raw content of something. In the most basic form, you send a file name to it.
xxd [filename]
So if you have a secret.txt file:
xxd secret.txt
This will release the contents of Secret.txt in hexadecimal along the ASCII representation. You can also transmit the flag -r to convert a hexagonal emptying into a binary file. At a certain level, we give you the hexadecimal emptying of a binary file. Using XXD, you must transform it into a zip file.
xxd -r data.txt data
This converts the text file to a binary file, provided that hexagonal emptying is in the right format.
ropes
Strings is a command line that extracts printable text from binary files. If you never open a strange appearance file and see a charabia wall, the ropes help to remove the readable bits such as passwords, indices or hidden messages. It is particularly useful when a file is not technically a text file, but always contains readable text somewhere inside.
strings secret_file
This will travel secret_file and print all the printable character sequences that he finds. In one of the levels, there is a file which contains text readable by the man hidden from a large piece of charabia. To filter the actual text, you must use the thong command on this file.
North Carolina
NC, abbreviation of Netcat, is a versatile networking utility that can read and write data on network connections using TCP or UDP. It is often called the “Swiss army knife” of networking tools because it can do so many things, such as the configuration of a simple server, the debugging ports or data reading from a socket.
nc host_ip port_number
This connects your machine to Port 1234 on Localhost, allowing you to send and receive raw texts or data. At a level, you are asked to submit a password to Port 30000 in Localhost. You can do this using the NC command.
nc localhost 30000
[Prompt to enter password]
This submits your password or any other data to the chosen port of the host name chosen.
My recommended way to play Overthewire
Not everyone learns the same way. And that’s good. If someone is absolutely new for Linux, it can find a little more difficult at first. However, there is a way to make it a little easier. It will also help you get the most out of this game.
Each level has a list of commands and certain basic concepts that you may have to erase to pass this level. My advice for you is not to precipitate the just level to finish it. Instead, take your time to read each concept to understand it correctly. The levels already connect the resources. If you still have doubts, do additional research.
The same goes for Linux orders. Read the man’s pages to understand each order and experience with them to understand their behavior. After that, jump at the first level and start your trip from there.
Whether you are new to Linux or you already like it, you should certainly consult Overthewire. No matter your skills, you will certainly learn something new too. There are so many other major resources to learn how to explore Linux.