What Is a Zip Bomb?

Summary
-
Compression in the ZIP archives minimizes data repetition by showing the original content.
-
Zip BOMBS uses compression, using recursion to create massive and revolutionary files of the system.
-
The detection and prevention of zip bombs require external strategies, such as limitation of depth and size of extraction.
You could open it by accident. But when it starts to decompress, your computer’s file system is blocking. Except that there is no malicious software in the ZIP archives, only mathematics.
How does compression work
When you compress a file in a zip archive, your computer is looking for models in 1 and 0. The repeated parts are stored once. Then, instead of writing the same thing again and again, the archive simply points to the original version. It is brutally effective. This is why text files tend to shrink so well. A few repeated strings can reduce megaoctets to kilo-kilo-kilo-kilo-kilob.
A zip bomb takes this logic and returns it against the computer.
Instead of a few repeated blocks, it includes a repeated block of millions of times. Again, the data itself is never copied, but the zip bombs the point again and again. Then he envelops this inside another archive. Then again. Then again.
When you reach the outer layer, it looks harmless. The file is tiny. He transfers quickly. There is nothing unusual. But once he starts to unpack, the references take place. Everyone opens on the next. The result is not a typical zip anti -archiving because it becomes an avalanche.
The famous
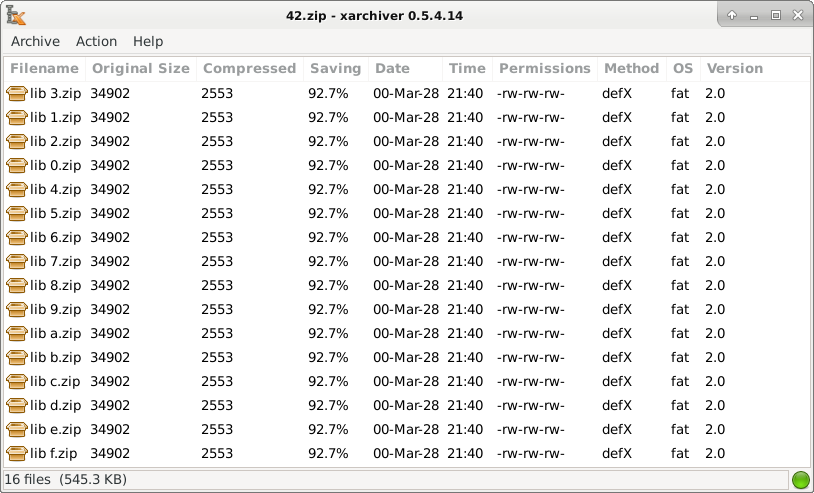
The best known zip bomb is called “forty-two zip points”. It only makes forty-two kilo-kilobbytes on disk. Inside, it contains sixteen archive files. Each of these contains sixteen others. All indicate the same piece of filling data. In terms of programming, this is called REDUSION. Think of mathematical recursion as a mirror room. One file opens another. This file once again opens the same file. Each layer follows the last. Nothing new is added. The structure continues to be called, again and again, until the system is short of space to keep track.
If you manage to decompress it completely, which most of the systems cannot do, the content extends to around four million and a half gigabytes. Archive 42.zip has never been supposed to infect anything. Its goal is to plant the tools that try to open it.
Why they still exist
Zip bombs are still used today, mainly in technical or research contexts. Some are used by safety testers to push the limits of the system. Some appear in academic work to explore the cutting -edge cases in compression. Some are sent during real cyber attacks, not as the attack itself, but as a distraction.
Modern zipped bombs use more recent tips. Some combine archive formats. Others include layers protected by password that confuse basic scanners. Some are divided on several e-mails, only dangerous when they went up.
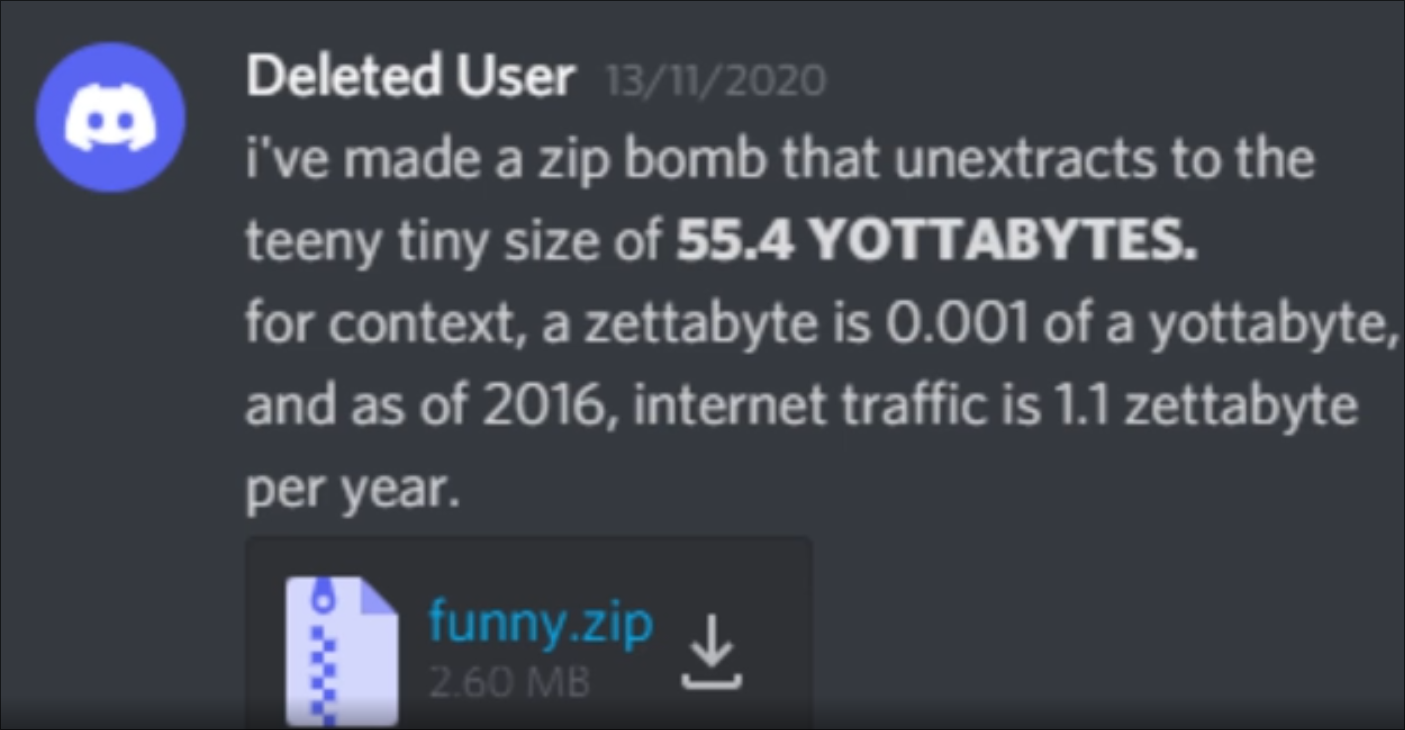
One of these archives, built in 2023, was ten megaoctes on disk. When it is completely extracted, it produced more than five million filling gigabytes.
Even right now, you can make one yourself. Write a script that archives files. Zip a file. Then zip the zip. Then zip it. Repeat it 100 times. The outdoor file always seems small. It always sends quickly by email. But each layer deepens the load.
Can you detect one?
The only protection is the strategy. There is no correction in the file itself. The archive is only harmless bits. Protection must come from outside.
Some systems stop decompressing after a few layers. Others refuse to extract more than a specific amount of data. Some tools are looking for repeated references to the same memory block.
Antivirus tools have also understood. They set limits: how depth they are going to scan, how will they unpack. But not all systems are protected. Sometimes it is a curious user. Sometimes it is automated. Anything that tries to decompress it is entirely the victim. And it works in WSL or Docker. The method is agnostic on operating systems.
If you write automation, limit decompression size. If you scan downloads, cap the depth. If you receive foreign files, do not trust the size or size of the file alone.
Legal? Technically
Zip bombs are open inside virtual machines, with killing switches and memory caps. The test is always isolated. The file never works on a live system.
A zip bomb is not a part code. It is not a script or an executable, so it is not a feat in the usual sense. It is a oddity of how modern computers work that a simple zip file without any executable can do any damage.
There is no law against sending a zip file without payload of viruses. But that doesn’t mean it’s legal. A zip bomb sent to crush a colleague’s computer is not a farce. It is a kind of sabotage. The courts tend to focus on the result, not on the type of file.
The real danger of a zip bomb is that it asks the system to work harder than it was supposed by overloading its file system. And most systems say yes. It’s the trick and the trap.